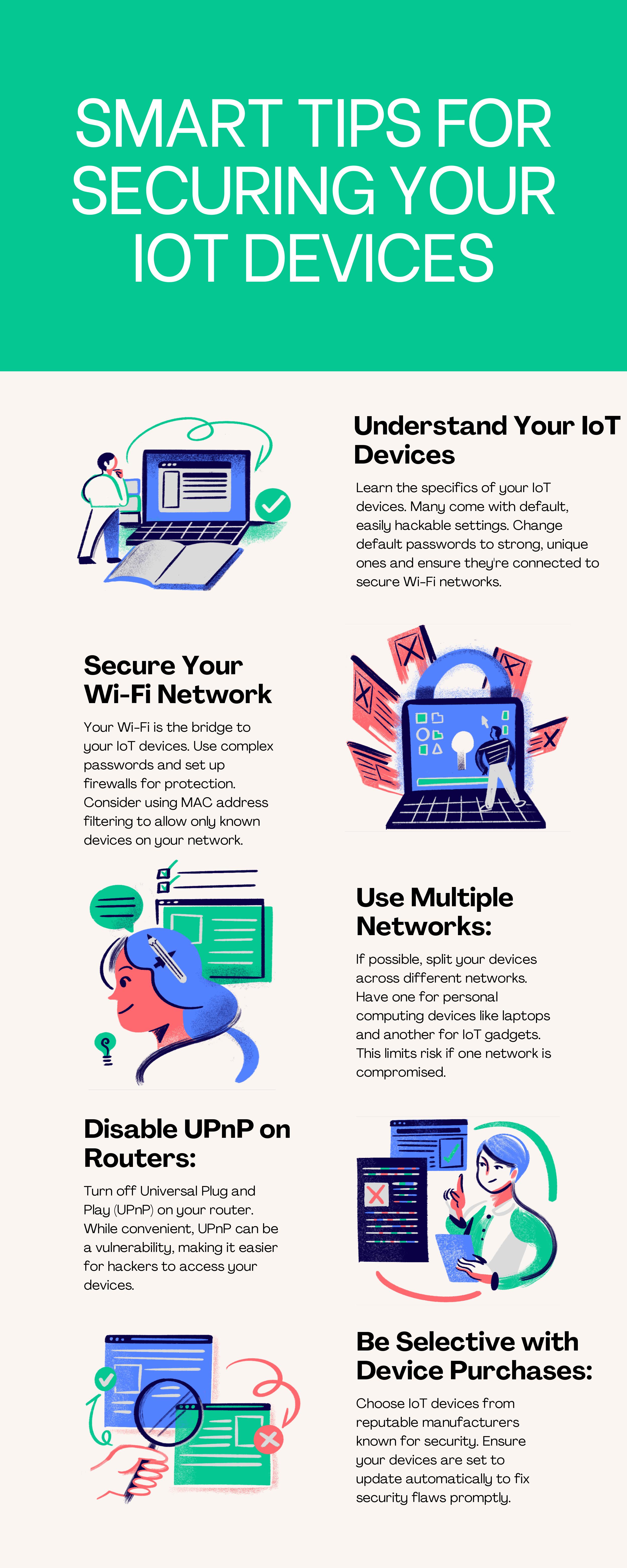
Tips and Techniques








Don’t Take the Bait
https://www.cisa.gov/secure-our-world/recognize-and-report-phishing
Phishing occurs when criminals try to get us to open harmful links, emails or attachments that could request our personal information or infect our devices. Phishing messages or “bait” usually come in the form of an email, text, direct message on social media or phone call. These messages are often designed to look like they come from a trusted person or organization, to get us to respond.
The good news is we can avoid the phish hook and keep our accounts secure with these tips!
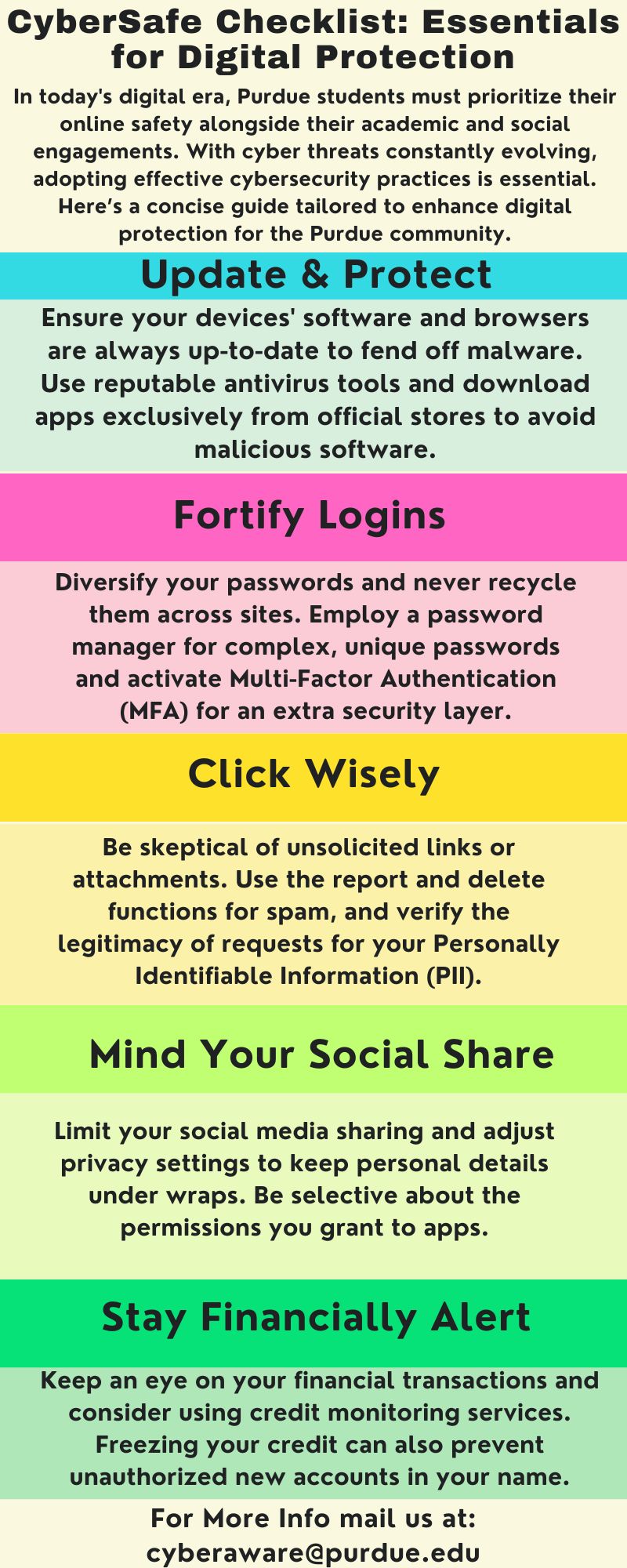
Stay Safe with Three Simple Tips
1. Recognize
Look for these common signs:
- Urgent or emotionally appealing language, especially messages that claim dire consequences for not responding immediately
- Requests to send personal and financial information
- Untrusted shortened URLs
- Incorrect email addresses or links, like amazan.com
A common sign used to be poor grammar or misspellings although in the era of artificial intelligence (AI) some emails will now have perfect grammar and spellings, so look out for the other signs.
2. Resist
If you suspect phishing, resist the temptation to click on links or attachments that seem too good to be true and may be trying to access your personal information. Instead, report the phish to protect yourself and others. Typically, you’ll find options to report near the person’s email address or username. You can also report via the “report spam” button in the toolbar or settings.
3. Delete
Delete the message. Don’t reply or click on any attachment or link, including any “unsubscribe” link. Just delete.

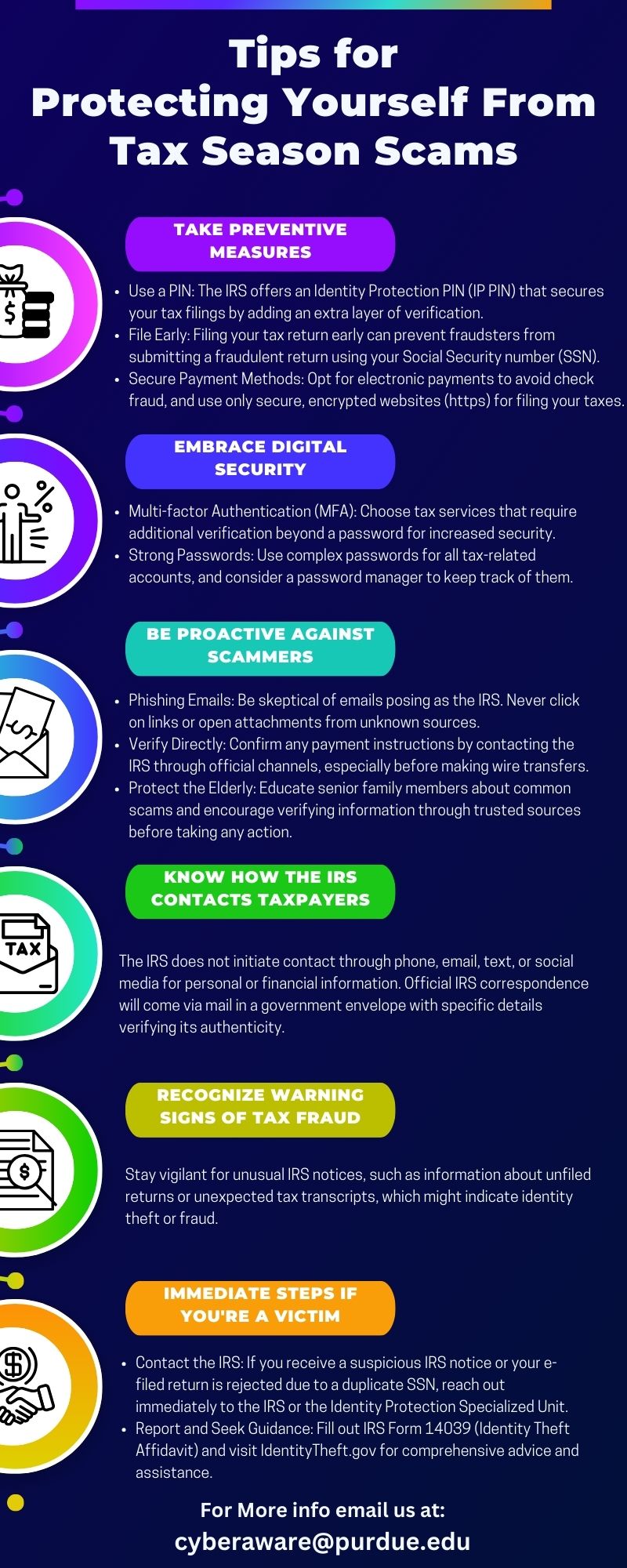



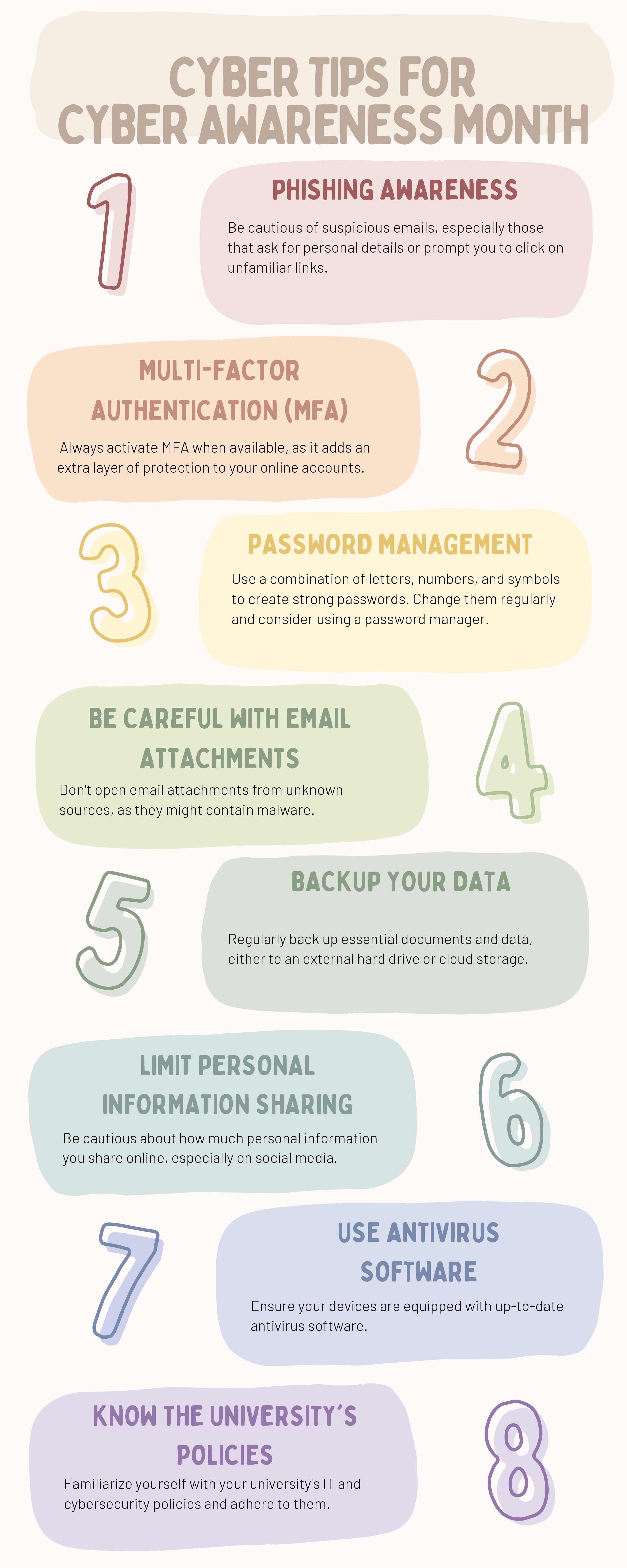
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) recently released a cybersecurity advisory related to Advanced Persistent Threat (APT) activity targeting Microsoft Outlook Online.
The advisory specifically urges businesses and organizations to enhance their monitoring capabilities and implement stronger security measures to detect and prevent this kind of intrusion. APTs are cyber threats characterized by stealthy and continuous computer hacking processes, often orchestrated by individuals or groups targeting a specific entity.
While specifics regarding the nature of the APT activity are not given in your query, the threats typically exploit vulnerabilities in systems, often seeking to gain unauthorized access, steal sensitive data, or disrupt services. In this case, since Outlook Online is being targeted, users' emails, contacts, and potentially other sensitive information could be at risk.
Here are some steps organizations and individuals could take in response to this advisory:
-
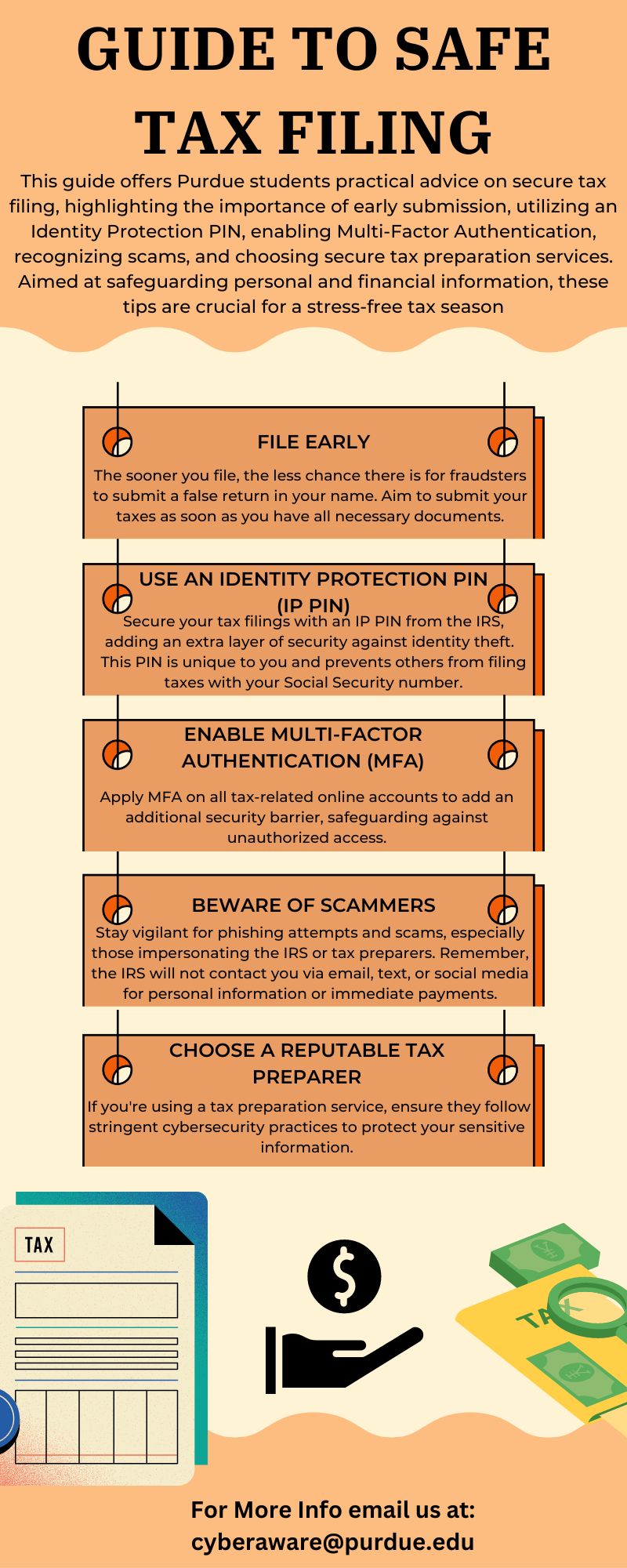
Update and Patch: Ensure your software, including Outlook Online, is always updated to the latest version. Regularly install patches, as they often fix security vulnerabilities that have been discovered.
-
Multi-Factor Authentication (MFA): Enable MFA where possible. This adds an additional layer of security by requiring more than just a password to access your account.
-
Regular Monitoring and Logging: Keep an eye on system logs, unusual network traffic, and any abnormal behavior, particularly for the Outlook Online service.
-
Security Awareness: Train employees to recognize and report potential phishing attempts, which are often the first step in an APT attack.
-
Incident Response Plan: Have a well-established incident response plan ready to ensure minimal impact in case of a security breach.
Remember, the best defense is a proactive one. Regularly updating and monitoring systems, along with strong security practices and regular backups, can provide significant protection against these types of threats. It's also recommended to work with a trusted cybersecurity partner to help manage and mitigate risks.

VPN:
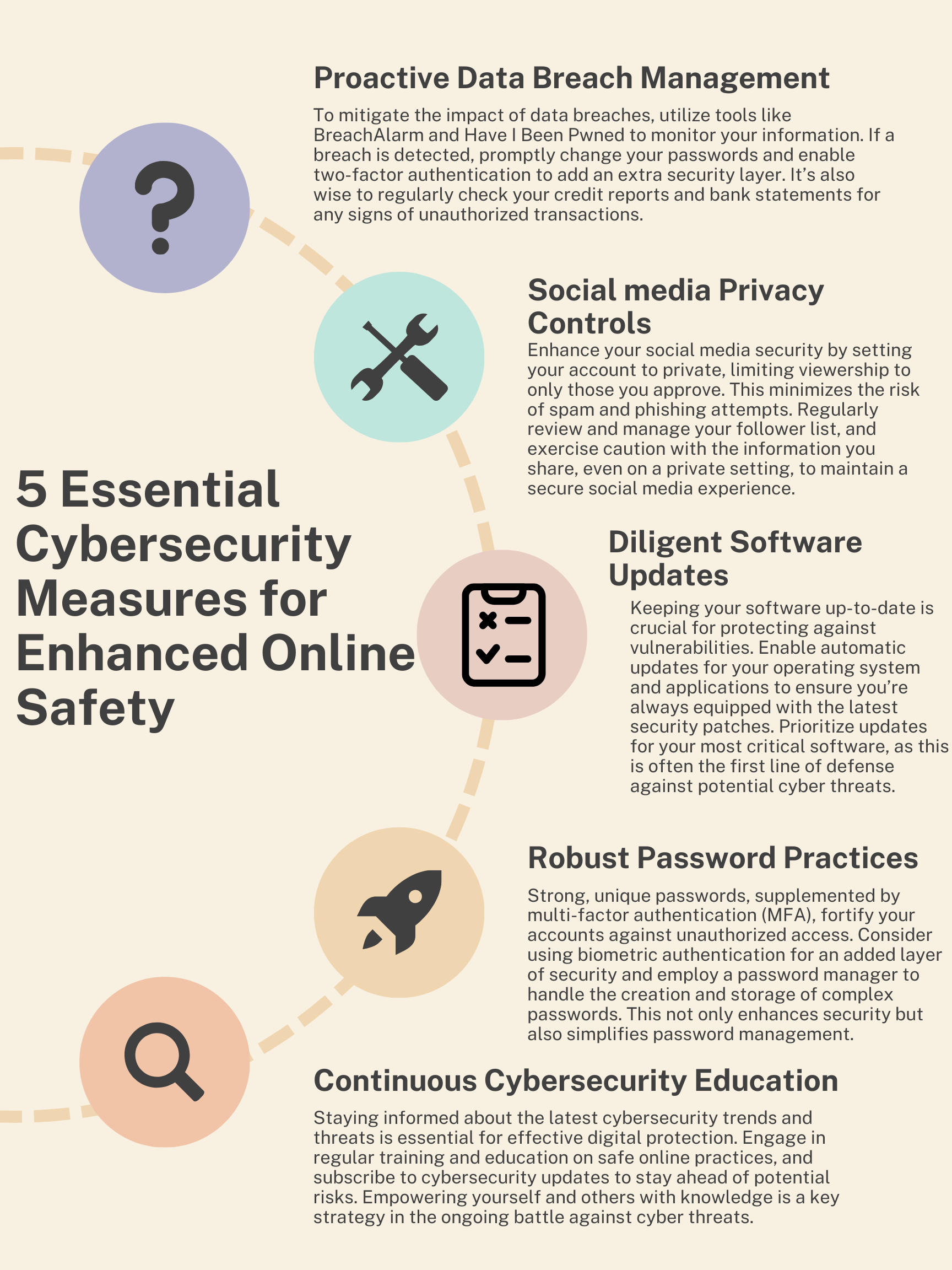
Using a VPN adds an extra layer of protection and makes it harder for anyone to see what you’re doing, since they won’t be able to find your IP address..
Suggestion would be Proton VPN:

Password Managers:
It is Mandatory to have different passwords for different mails and accounts. But it is hard to remember all those passwords and passcodes. Hence the usage of password manager comes handy.
Suggestions for the Password Manager would be bitwarden:

Anti-Virus:
It is also better to have a good Anti-virus installed in our system to keep the malwares and virus away. As even if we stay safe in web, there are possibility for virus, malwares and click wares affecting our system.
Suggestions for Anti-virus would be Malwarebytes:

The links below are to tools available for general use in managing your privacy when browsing the web. These tools have not been evaluated by Purdue. Before using these or any other Web privacy tools, please be sure to read their privacy notices and seek out reviews to ensure the tool is safe, up to date, and continuing to operate effectively.
- Cybersecurity Awareness
- Threats
- Cybersecurity Updates
- Cybersecurity FAQ